Audit methods
AlloyScan offers two methods for conducting audits: agent-based and agentless. This article describes the advantages of each method and explains how to choose the most suitable method for the specific network configuration and auditing requirements.
Both methods are visually represented in the diagram below, with detailed explanations provided in their respective sections. You will also find below a comparative table summarizing the differences between the two methods for quick reference.
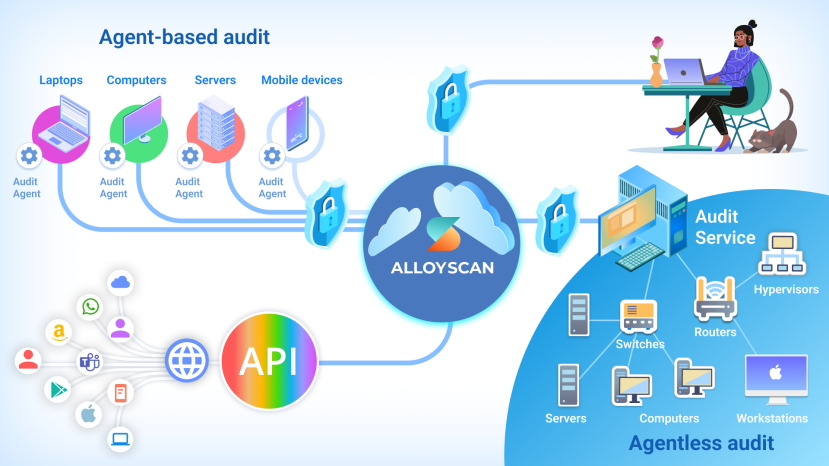
Agent-based method
In the agent-based method, users install an audit agent on each device they wish to track within their network. This could include devices such as laptops belonging to remote employees, as well as desktops and servers within the organization's network infrastructure. The only requirement for this method is access to the internet.
Agentless method
The agentless method operates within logical units of your infrastructure referred to in AlloyScan as segments. By designating a single computer within the segment and installing the Audit Service on it, you can remotely discover every IT asset, software, and hardware component present in that segment. The Audit Service acts as a proxy, crawling the network to identify connected devices like routers and printers, and collecting and reporting their inventory data to AlloyScan.
This method does not require the installation of any agents on individual devices. To implement the agentless method, you need to open specific ports and enable certain protocols in the designated segment (see Required ports for agentless audit).
Flexibility and compatibility
You can choose either the agent-based method, the agentless method, or a combination of both, depending on their specific auditing requirements and network configuration. Regardless of the chosen method, the data collected and reported from the audit remains consistent.
| Agent-based | Agentless | |
| What IT assets do you want to track? | ||
| Computers: Servers, workstations, desktops, laptops |
Yes |
Yes |
| Mobile devices: Smartphones and tablets | Planned | |
| Network devices: Routers, switches, printers, network cameras, etc. | Yes | |
| Hypervisors | Yes | |
| Cloud resources: Containters, cloud instances, cloud servers | Planned | |
| Where are the IT assets that you want to track? | ||
| Within the local network: Your office, school, store, etc. | Yes | Yes |
| Within a remote network: An office branch, warehouse, factory, etc. | Yes | Yes |
| Offsite: Remote employees' homes or flexible work locations | Yes | |
| In Cloud: Azure, AWS, or another cloud service | Planned | |
| What platforms do you want to audit? | ||
| Windows | Yes | Yes |
| Linux | Yes | Yes |
| macOS | Yes | Yes |
| vSphere/ESXi, Citrix, Xen, Hyper-V | Yes | |
| iOS | Planned | |
| Android | Planned | |
Watch this quick guided tour to discover the available audit methods and see how to get started with each one.