Understanding LDAP Authentication
LDAP (Lightweight Directory Access Protocol) authentication enables you to use the existing LDAP server as a consolidated data source for user data. It streamlines the login process and automates administrative tasks: you can save time on creating user accounts and assigning their roles.
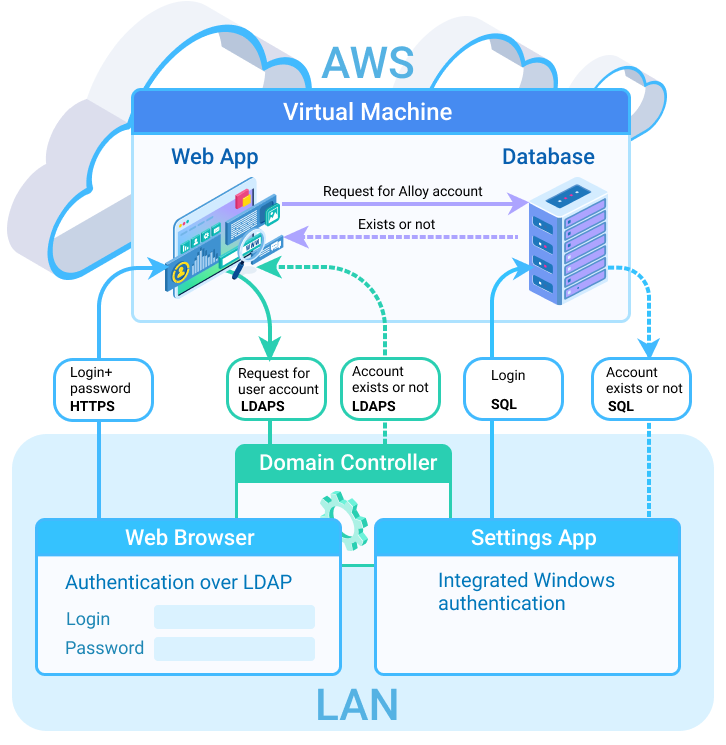
The mechanism uses the read-only LDAP service account credentials to retrieve the username from the LDAP server. The password that the user enters in the browser to the web application is contained entirely in the HTTPS session. The application only requests for information to the domain controller over the LDAPS, and then updates its internal database accordingly. No changes are made to the internal LDAP server by the instance. If the user exists in the Active Directory, the application sends a request to the database, looking for the matching user account. When the requested user is found, the authentication occurs.
The authentication mechanism works as follows:
-
A user opens a web application (the Web App, Mobile App, or the Self Service Portal) in a web browser and enters the credentials: login and password.
-
The browser sends the credentials to the application over HTTPS.
-
The application sends a request for information to the domain controller over LDAPS. The app searches for the corresponding domain record in the Alloy Navigator by the entered domain name.
-
If the domain record exists, the application looks up for the user account in the specified directory service container.
-
If the user account is found in the Active Directory, the application queries the Alloy Navigator database to see whether that user has an Alloy account.
- If a matching account exists and is active, the authentication occurs and the web application lets the user in.
INFO: For instructions on enabling LDAP authentication, see Enabling LDAP Authentication.